This Item Ships For Free!
Spring security configuration top
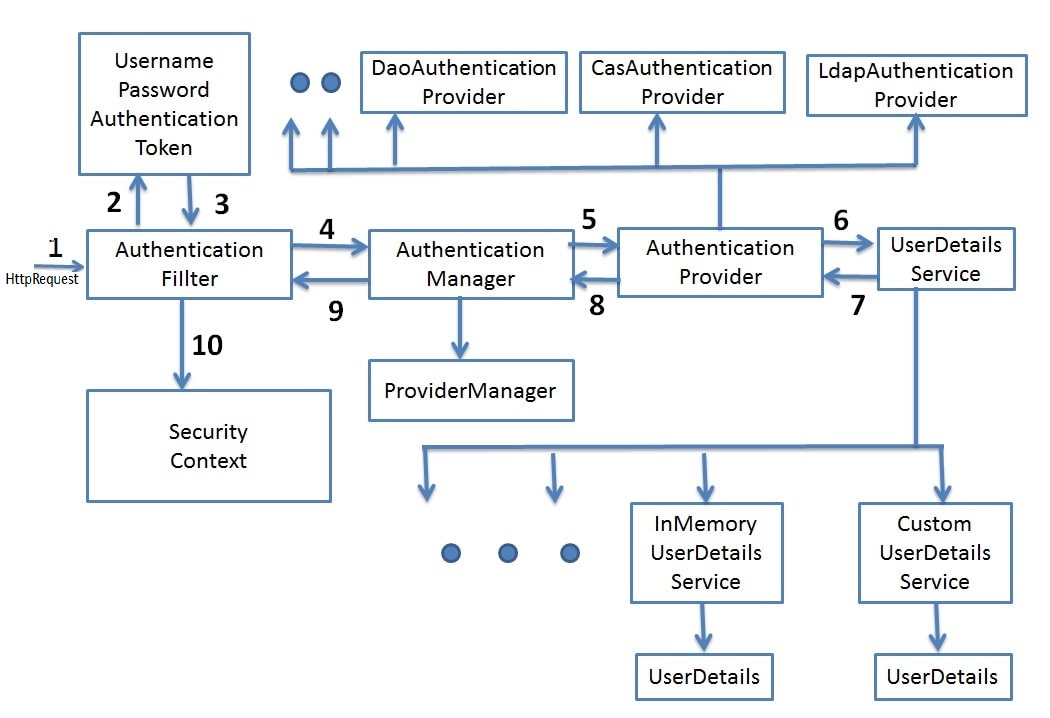
Spring security configuration top, Spring Boot Security Configuration practically explained Part1 Starting with Spring Boot Security and Basic HTTP Authentication Panos Zafiropoulos DevXperiences top
4.79
Spring security configuration top
Best useBest Use Learn More
All AroundAll Around
Max CushionMax Cushion
SurfaceSurface Learn More
Roads & PavementRoads & Pavement
StabilityStability Learn More
Neutral
Stable
CushioningCushioning Learn More
Barefoot
Minimal
Low
Medium
High
Maximal
Product Details:
Product code: Spring security configuration topDemystifying Spring Security setup by Boudhayan Dev Medium top, Spring Security Java Configuration Annotation Example Dinesh on Java top, 6.1. Spring Security Overview TERASOLUNA Server Framework for Java 5.x Development Guideline 5.0.1.RELEASE documentation top, Spring Security in Motion Part 1 by Kondah Mouad Geek Culture Medium top, Spring Security JWT Tutorial Toptal top, Spring Security Reference top, Spring Security Tutorial updated for Spring 6.x top, Spring Security Tutorial Learn Step to Secure Web Dinesh on Java top, Securing the Gates Basic Configuration and Authentication in Spring Security 6 top, Spring Boot Security Configuration practically explained Part1 Starting with Spring Boot Security and Basic HTTP Authentication Panos Zafiropoulos DevXperiences top, 6.2. Spring Security Tutorial TERASOLUNA Server Framework for Java 5.x Development Guideline 5.0.0.RELEASE documentation top, Explain Spring Security architecture and working IT Guru top, Architecture Spring Security top, Spring Security Architecture GeeksforGeeks top, Spring sale security configuration top, SpringSecurity Part 3 Spring Security Flow by Himaanshu Shukla Medium top, Introduction to Spring Security by Pritam Kumar Dev Genius top, Spring Security Authentication Architecture Explained In Depth top, Spring Security architecture Hyperskill top, Spring security config defaultsuccessurl annotation Stack Overflow top, Authorization Architecture Spring Security top, Configure Spring Security to use SecurityFilterChain and Spring Security Lambda DSL Huong Dan Java top, Spring Boot Security Configuration practically explained Part1 Starting with Spring Boot Security and Basic HTTP Authentication Panos Zafiropoulos DevXperiences top, Spring Security The Security Filter Chain by Kasun Dissanayake Medium top, Angular 8 Spring Boot JWT Authentication with Spring Security example BezKoder top, Spring Boot Spring Security JWT MySQL Database Tutorial top, Custom Authentication Filter with Spring Security Backendhance top, WebSecurityConfigurerAdapter Deprecated In Spring Security JavaTechOnline top, Top Spring Security Interview Questions 2024 InterviewBit top, Spring Security Authentication and Authorization In Depth top, java Configure datasource for integrating Spring Security in existing Spring project Stack Overflow top, In memory sale spring security top, Spring Security top, Spring actuator security top configuration top, Spring Security Authentication Architecture Explained In Depth top.
- Increased inherent stability
- Smooth transitions
- All day comfort
Model Number: SKU#7311864
Specs & Fit
Spring security configuration top
How It Fits
Spring sale security configuration- spring security configuration
- spring security cookie authentication
- spring security cookie based authentication
- spring security cross site scripting
- spring security custom login
- spring security database
- spring security database authentication
- spring security database authentication example
- spring security database authentication spring boot
- spring security database example